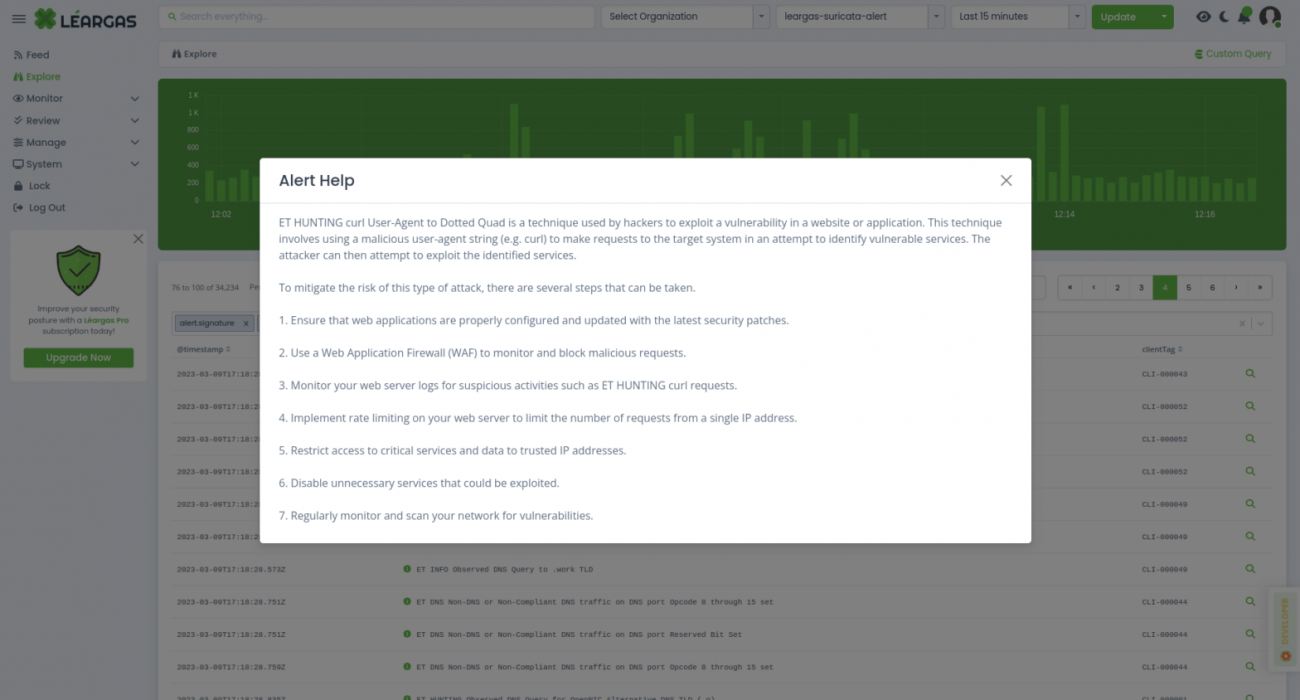
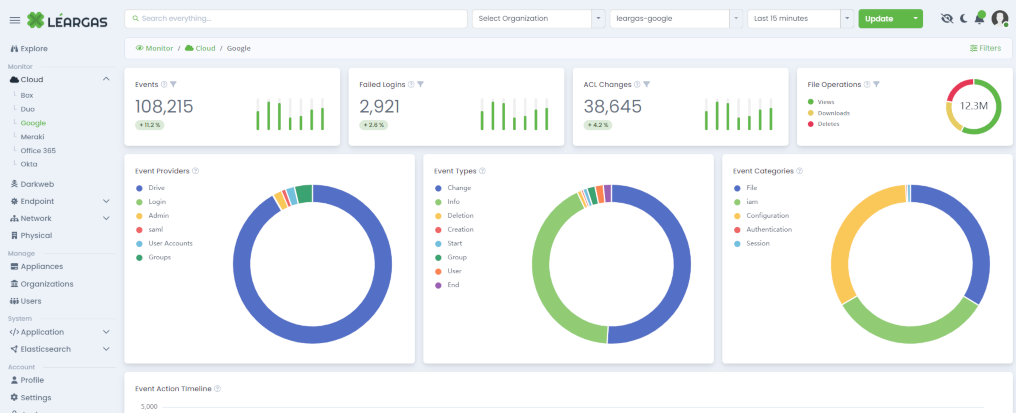
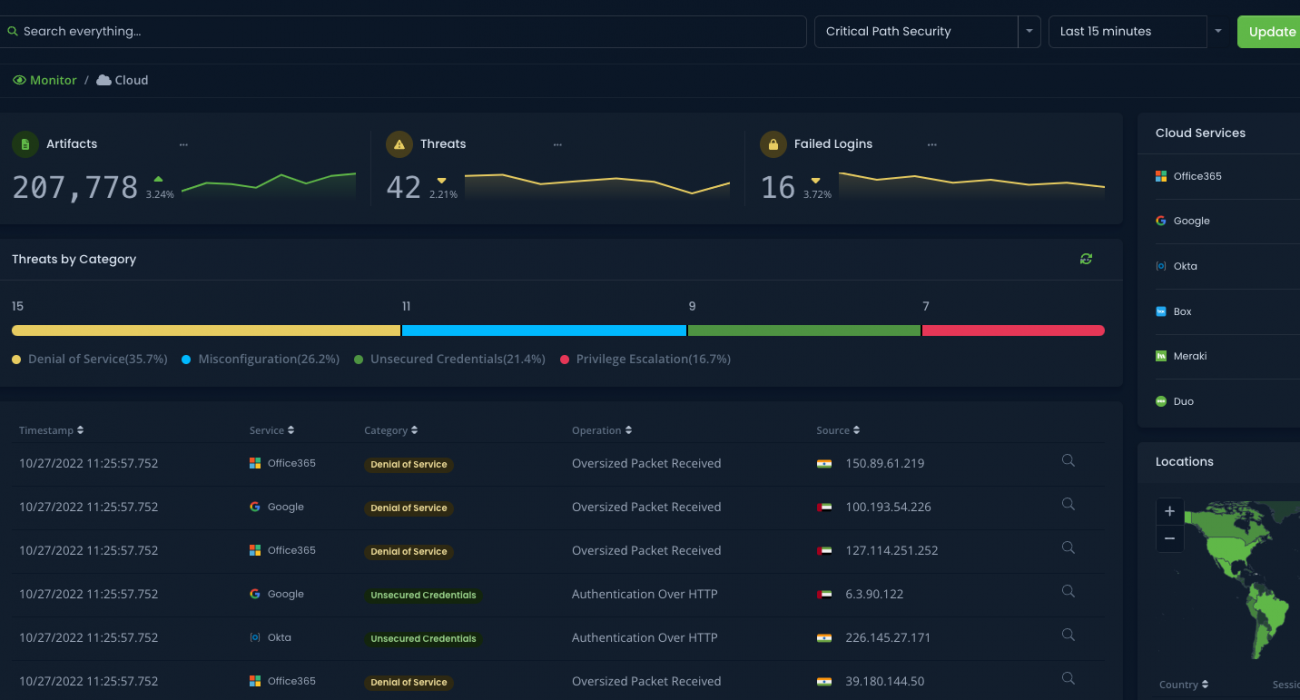
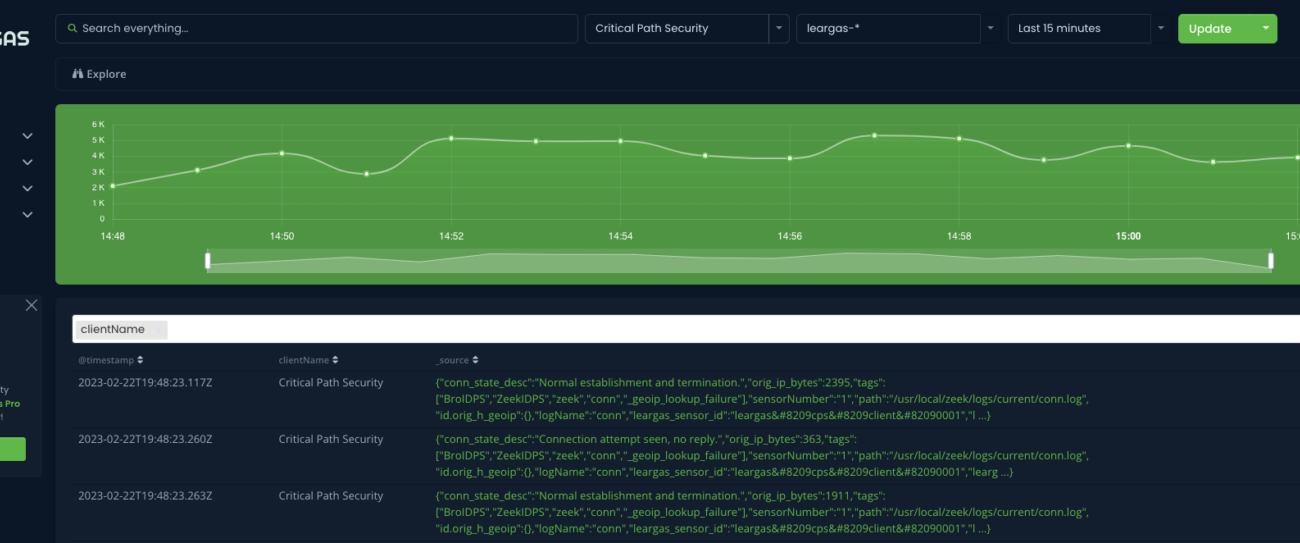
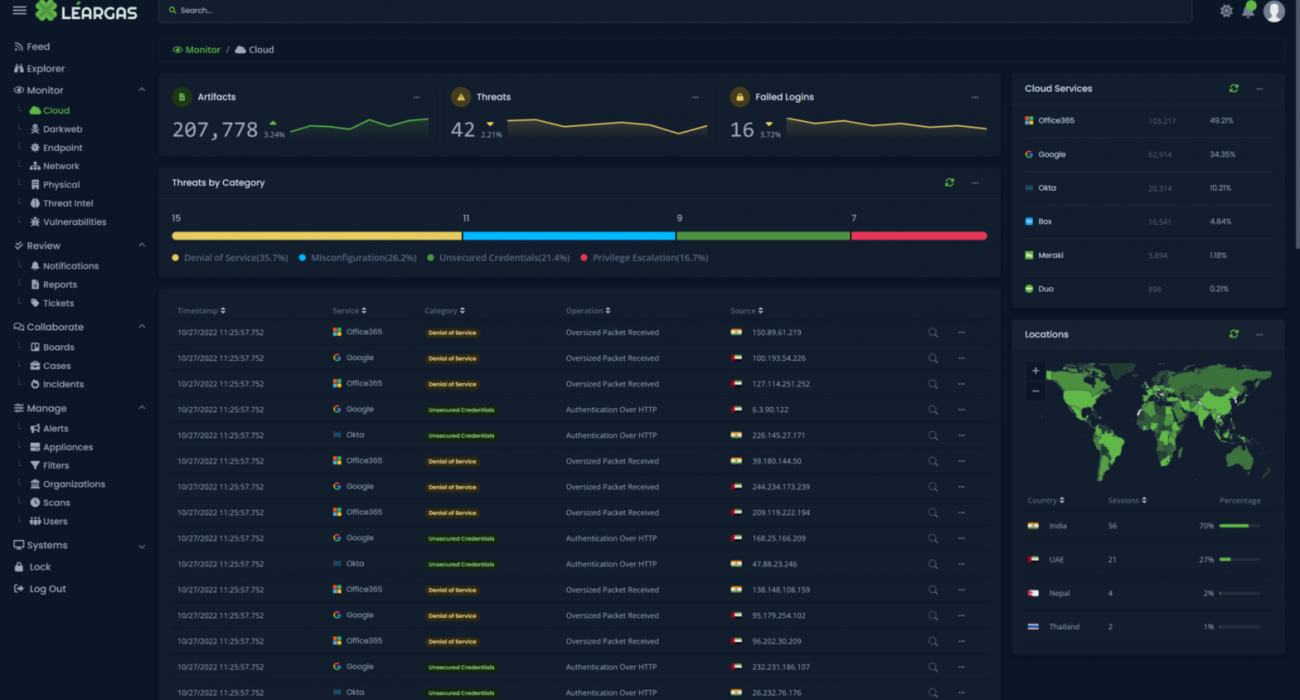
Léargas Security with AI – The Dawn Of A New Age In Cybersecurity
BLOG Léargas Security with AI – The Dawn Of A New Age In Cybersecurity For a long time, “artificial intelligence” has been a popular buzzword in the cybersecurity sector, boasting solutions capable of detecting suspicious network activities, rapidly understanding the situation, and assisting in incident response upon an intrusion. However, [...]