SCENARIOS SHOWCASE
Discover firsthand the transformative impact of Léargas solutions through our detailed case studies.
Each story showcases the innovative ways our clients harness the power of Léargas to fortify their security infrastructure and streamline operations.
EXPLORE OUR CASE STUDIES
Real-time Correlation with Vulnerability Scan Metrics
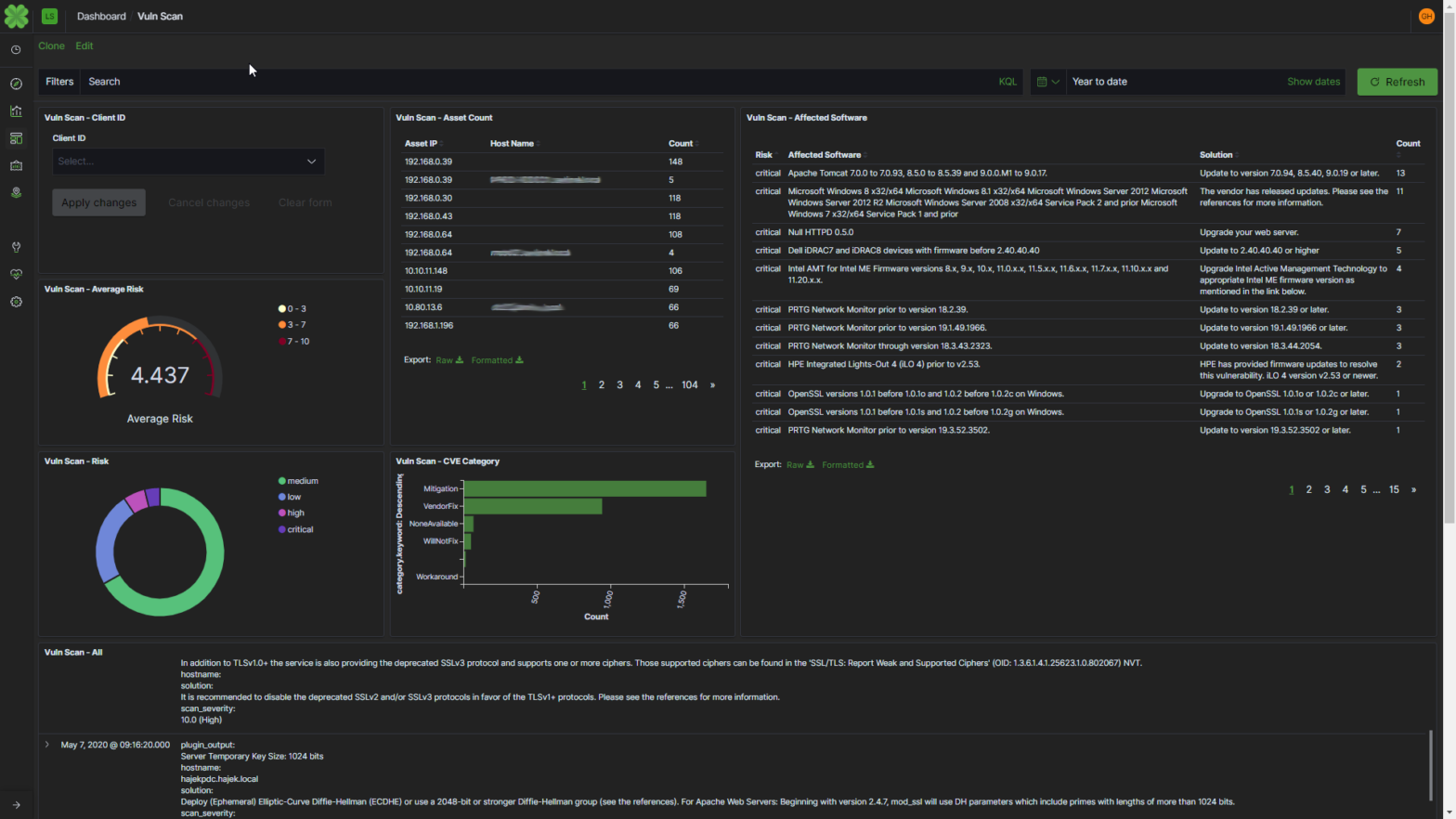
Léargas is proud to announce its latest platform enhancement; Real-time Correlation with vulnerability scans to further increase the accuracy and confidence of alerts.
Data correlation has always been at the heart of Léargas, and this added functionality makes use of the platform's foundation to tag alerts and notices on the fly with relevant information from the latest vulnerability scans.
This feature has reduced the number of false positives and increased overall confidence in our notifications and alerts. Additionally, this information becomes immediately available to drive next steps in our escalation and remediation process, enhancing network security and further reducing dwell time of attacks.
Just another way Léargas is providing insight.
Leveraging CIRCL's AIL Framework and Leargas Security XDR Platform for Effective Breach Discovery and Management
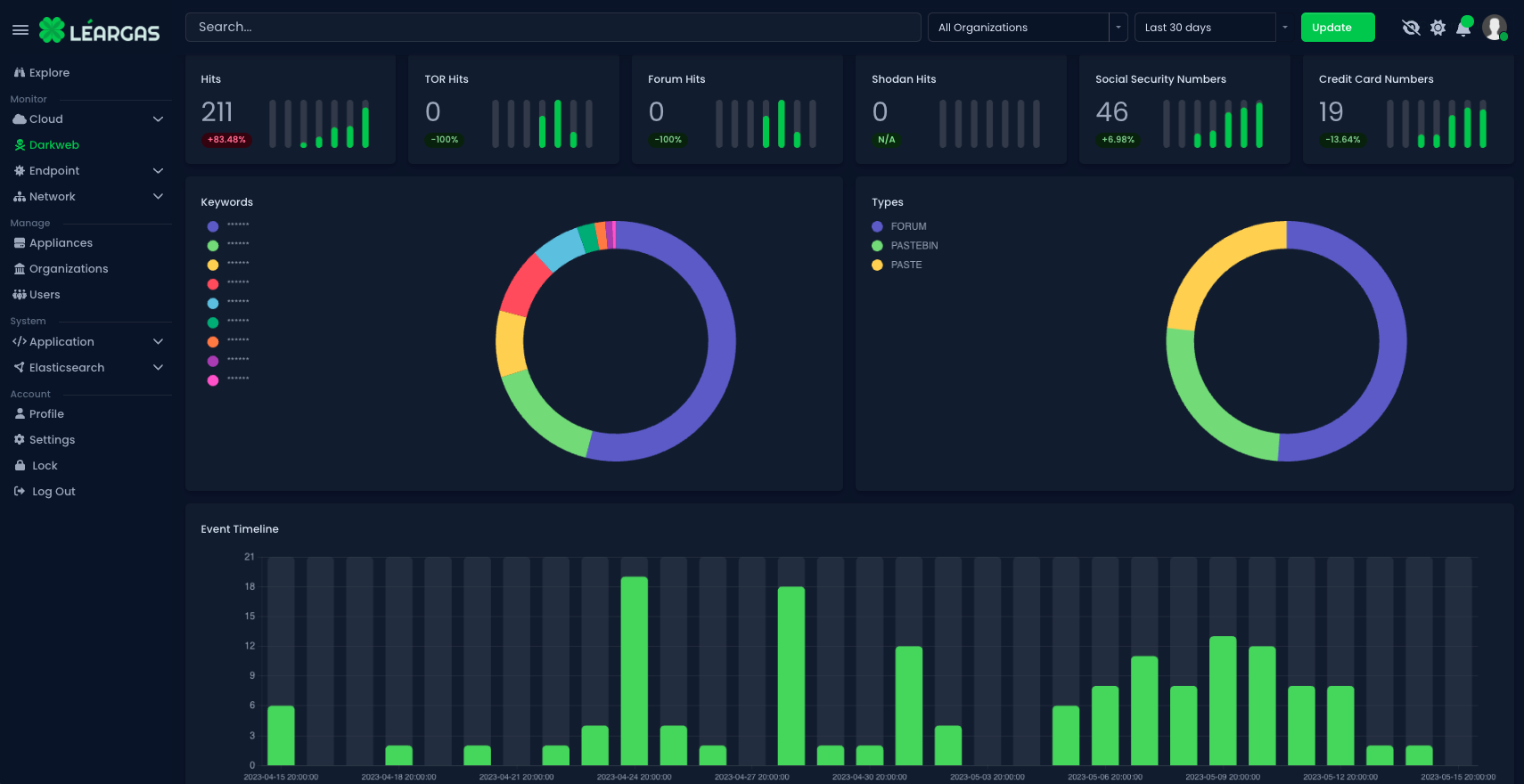
As the digital landscape expands, so does the complexity and magnitude of cybersecurity threats. This shift has led to the development of sophisticated cybersecurity tools designed to detect, manage, and respond to potential security breaches. Two such tools making waves in the cybersecurity field are the Computer Incident Response Center Luxembourg (CIRCL) Analysis Information Leak (AIL) framework and the Leargas Security Extended Detection and Response (XDR) platform.
These tools, when utilized in combination, can provide a comprehensive solution to cybersecurity threats, facilitating effective breach discovery and management.
Understanding the CIRCL AIL Framework
The CIRCL AIL framework is an innovative tool designed to analyze potential information leaks from unstructured data sources. The framework was developed by CIRCL, a government-driven initiative in Luxembourg that provides a wide range of services to help organizations protect their information systems. The AIL framework is capable of identifying credit card numbers, email addresses, URLs, and other sensitive information that may be leaked and thus put the organization at risk.
This framework uses a multi-layer approach, with each layer responsible for a specific aspect of data analysis. The first layer captures data from various sources, while the second layer processes the data to extract relevant information. The third layer is responsible for classifying and storing this information, and the final layer includes a user interface that presents the results in a simple, easy-to-understand format.
Leargas Security XDR Platform
On the other hand, the Leargas Security XDR platform is a sophisticated cybersecurity tool designed to automatically detect, investigate, and respond to threats across various data sources. This platform integrates several security technologies - including endpoint protection, network security, and cloud security - into a unified system that provides comprehensive visibility and control over the organization's security environment.
One of the major advantages of the Leargas Security XDR platform is its ability to correlate data from different sources, making it easier to identify complex threats that might go unnoticed in a more siloed security environment. This platform uses advanced analytics and machine learning algorithms to detect anomalies and flag potential threats, enabling security teams to respond quickly and effectively.
The Synergy between AIL and XDR
By combining the power of the CIRCL AIL framework and the Leargas Security XDR platform, organizations can significantly enhance their cybersecurity posture.
The AIL framework can feed its findings into the XDR platform, which can then correlate this information with data from other sources to provide a more comprehensive picture of the organization's security environment. For instance, if the AIL framework identifies a potential information leak, the XDR platform can use this information to help pinpoint the source of the breach and determine its impact.
Additionally, the XDR platform's automated response capabilities can help mitigate the damage caused by a security breach. If the AIL framework detects a leak, the XDR platform can automatically take steps to isolate affected systems, block malicious traffic, or even initiate incident response procedures.
Conclusion
The combination of the CIRCL AIL framework and the Leargas Security XDR platform offers a promising solution to the complex challenges posed by today's cybersecurity threats. By providing comprehensive visibility into potential information leaks and the ability to respond quickly and effectively, these tools can help organizations protect their valuable data and maintain the trust of their stakeholders. As cybersecurity threats continue to evolve, the importance of using such sophisticated and integrated tools cannot be overstated.
For potential customers interested in fortifying their cybersecurity architecture, reach out!
Léargas Security with ChatGPT – The Dawn Of A New Age In Cybersecurity
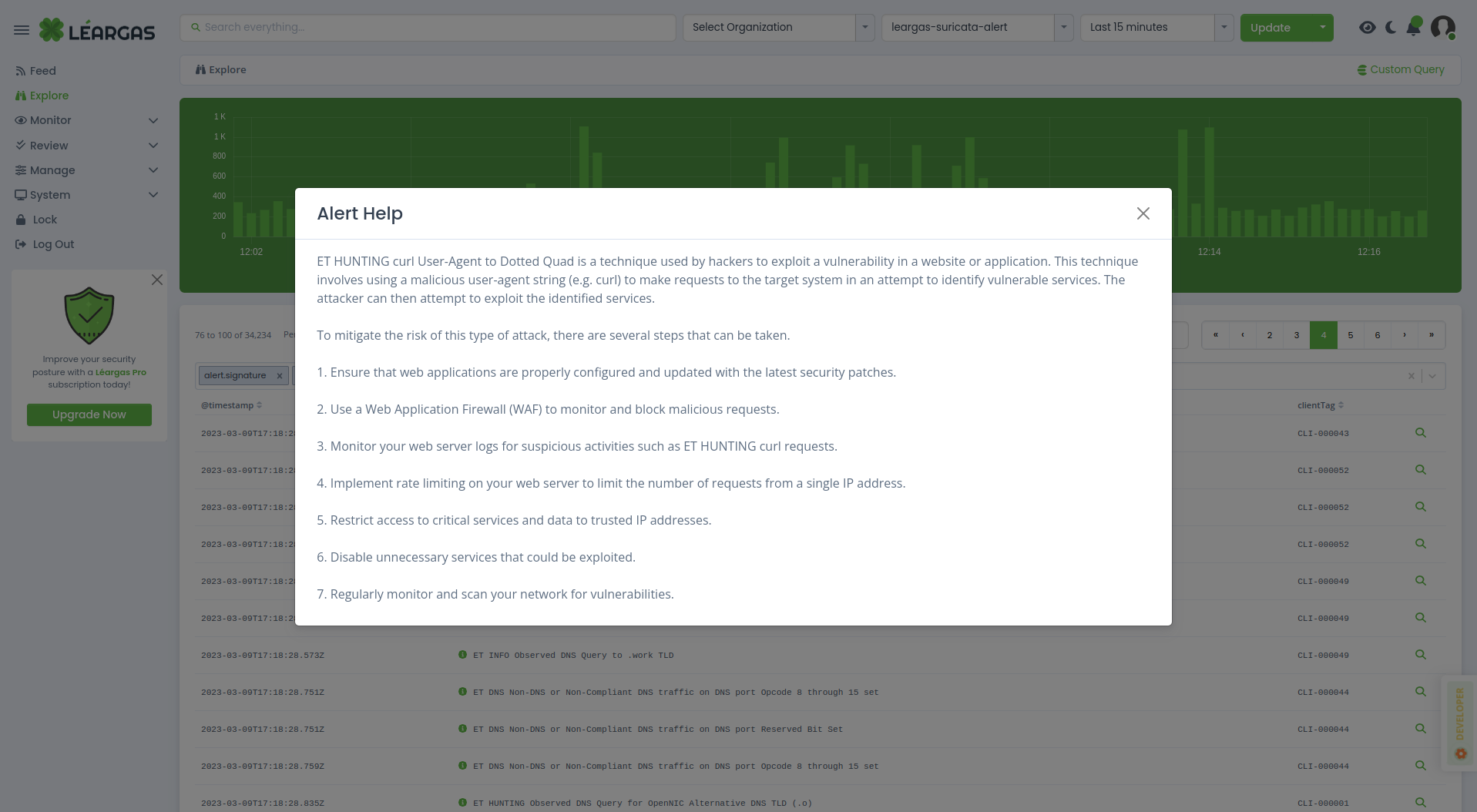
For a long time, "artificial intelligence" has been a popular buzzword in the cybersecurity sector, boasting solutions capable of detecting suspicious network activities, rapidly understanding the situation, and assisting in incident response upon an intrusion. However, the most effective and reliable services so far have been machine learning algorithms designed to identify malware traits and other questionable network behaviors. Now, with the increasing availability of generative AI tools, Léargas Security has finally developed a service for security professionals that lives up to the hype.
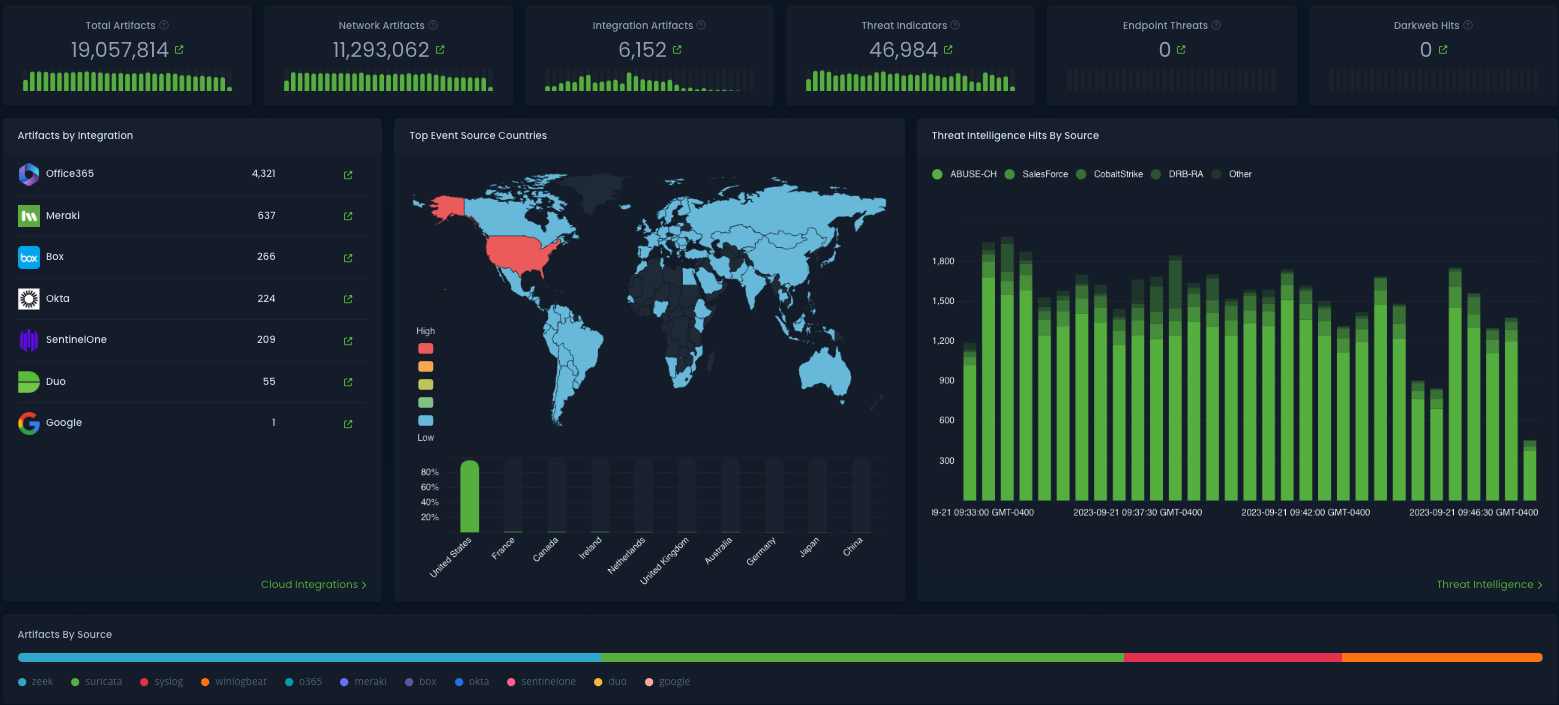
A few weeks ago, Léargas introduced the integration of ChatGPT into the Léargas Security platform, a product that leverages ChatGPT and their own work on large language models. Léargas is now releasing the platform which integrates system data and network monitoring from security solutions like Zeek, Suricata, Windows Event Logs, Syslog, Wazuh, OSSEC, Google Workspaces, AWS, Azure, Office365, Box, DUO, OKTA as well as many third-party services.
Léargas Security generates alerts, visually and textually represent network activities, and offer steps for potential investigations. As an analyst leverages Léargas Security to analyze a possible security incident, the platform keeps track of the history, allowing added team members to quickly catch up and review the progress made.
Primary Goals and Objectives:
Léargas Security's capabilities encompass:
The Léargas Security provides access controls that enable selective sharing of specific projects with certain colleagues, which is crucial when investigating potential insider threats. Additionally, Léargas Security serves as a round-the-clock monitoring support system. This ensures that even in the absence of an expert with a particular skillset during a shift or day, the system can offer fundamental analysis and recommendations to address any gaps.
For instance, if a team needs to promptly examine a potentially malicious network flow or software binary, Léargas Security can initiate the analysis, contextualize the behavior, and determine its possible objectives.
Want to know more? Schedule a demo today!
Correlation and Enrichment: Office365 and Endpoint Security
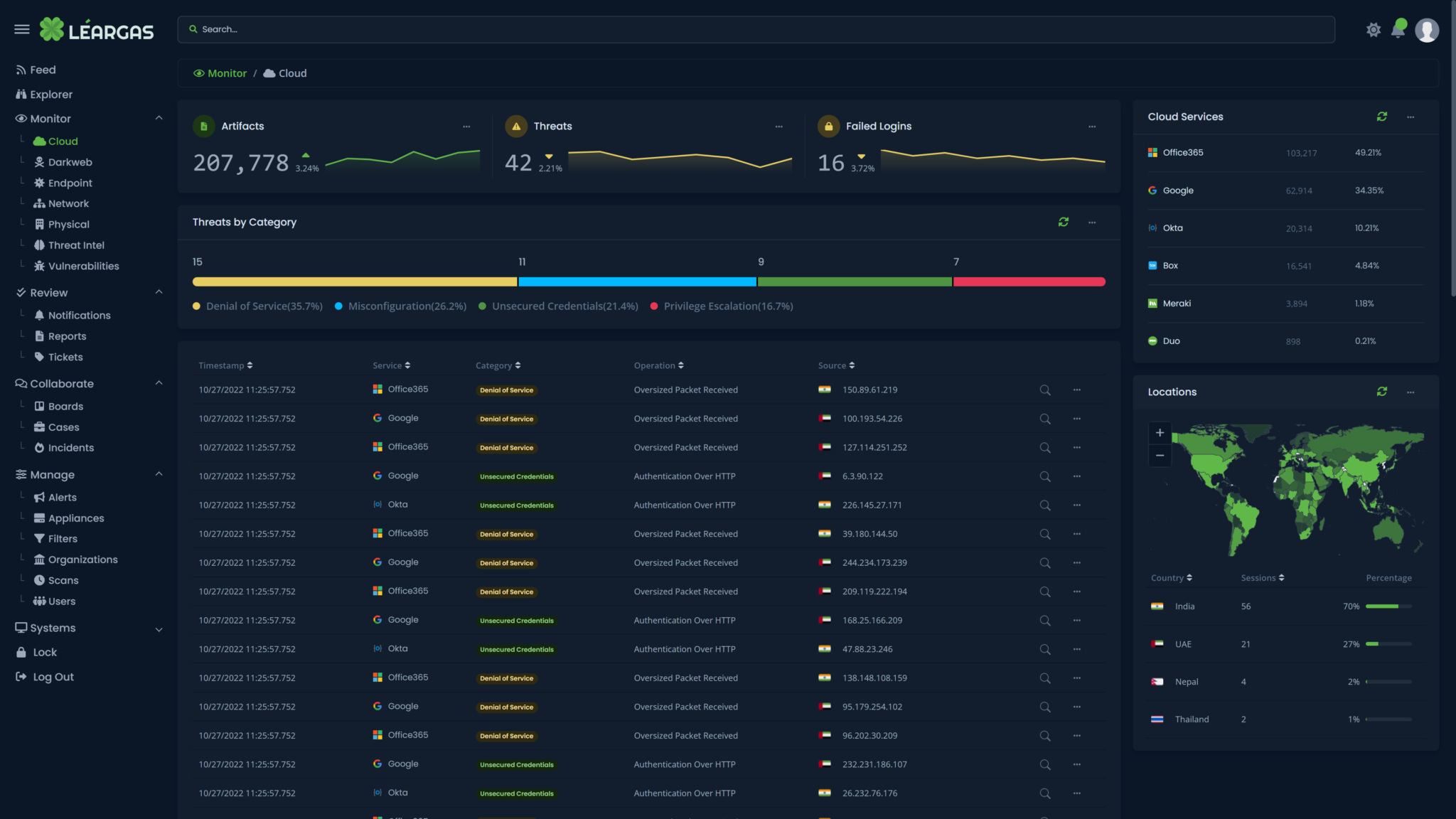
As organizations increasingly rely on cloud-based services such as Office 365 for their productivity and collaboration needs, it's critical to understand the importance of correlating logs from both the cloud service and the endpoint devices. This correlation can provide a comprehensive view of the activities taking place within the organization and help ensure the security and compliance of sensitive information, no matter where the endpoint might be.
One of the main benefits of correlating Office 365 and Endpoint Security logs is that it can help identify suspicious or malicious activity. For example, if a user's endpoint device shows signs of a security breach, geographically-impossible authentication attempts, or attacks such as a virus or malware event, the corresponding Office 365 logs can provide valuable information on what data may have been accessed or exfiltrated.
The Léargas Security platform automatically correlates the data from the sources into single searches and alerts.
Additionally, correlating Office 365 and Endpoint Security logs can also help organizations identify compliance violations, such as unauthorized access to sensitive information. With the right tools, organizations can quickly identify when a user has taken actions that violate their data protection policies, such as downloading confidential data onto a personal device or sending sensitive information to an unauthorized email recipient.
Moreover, correlating logs can help improve incident response time. In the event of a security incident, having a comprehensive view of the activities that took place can help organizations quickly identify the source and scope of the problem, enabling them to respond and resolve the issue more efficiently.
Here are the Top 10 reasons for automatically correlating Office 365 and Endpoint Security logs:
- Improved visibility into user activity: Correlating logs provides a comprehensive view of what users are doing within the organization, including access to sensitive information and email correspondence, regardless of location and time.
- Detecting suspicious or malicious activity: Correlating logs can help identify potential security threats and unauthorized access to sensitive data.
- Improving incident response time: Having a comprehensive view of activities can help organizations quickly identify the source and scope of security incidents, allowing them to respond more efficiently.
- Ensuring compliance with industry regulations: Organizations can use log data to demonstrate compliance with regulations such as GDPR and HIPAA.
- Auditing and compliance reporting: Log data can provide valuable insights for auditing and compliance reporting, helping organizations ensure that their security and privacy practices are up to standards.
- Protecting sensitive data: Correlating logs can help organizations identify when sensitive data is being accessed, downloaded, or sent to unauthorized recipients, allowing them to take appropriate action to protect it.
- Detecting endpoint security breaches: Endpoint devices are a common target for attackers, and correlating logs can help organizations identify when a device has been compromised and what data may have been accessed.
- Identifying unusual user behavior: Correlating logs can help organizations identify when users are engaging in suspicious or unusual behavior, allowing them to take appropriate action to mitigate potential threats.
- Detecting data exfiltration: By tracking user activities, organizations can identify when sensitive data is being exfiltrated and take appropriate action to prevent it.
- Enhancing security and privacy: By correlating logs, organizations can gain a better understanding of their security and privacy practices and take appropriate steps to improve them.
Finally, correlating Office 365 and Endpoint Security logs can also provide valuable insights for auditing and compliance reporting. Organizations can use the data from these logs to demonstrate their compliance with industry regulations and standards, such as GDPR and HIPAA, by providing a detailed view of their security and privacy practices.
Revolutionizing Energy Cooperatives: The Value of Leargas Security XDR

As the globe becomes progressively dependent on digital systems and automation, cybersecurity has evolved into a pressing issue for all organizations. This trend is not just applicable to major corporations or tech firms; it is equally relevant to entities like energy cooperatives. Given their key responsibility in delivering vital services to communities, these cooperatives cannot afford to overlook the importance of robust cybersecurity measures.
Energy cooperatives, in particular, are attractive targets for cyber threats. Their distinctive position, acting as the backbone of essential services for local communities, makes them an appealing focus for cybercriminals. If these threats are not effectively countered, the implications can be severe. A successful cyber-attack could potentially disrupt the services of the cooperative, leading to dire consequences for the communities they serve.
Within this challenging scenario, Leargas Security XDR has risen as a crucial solution to these prevalent risks. This platform, with its advanced cybersecurity capabilities, effectively neutralizes the threat of cyber-attacks on energy cooperatives. By doing so, it underscores the value of strong cybersecurity measures, ensuring that energy cooperatives can continue to serve their communities without disruption.
Understanding Leargas Security XDR
Leargas Security XDR (eXtended Detection and Response) is a unified cybersecurity solution that integrates multiple protection tools into a single platform. It goes beyond traditional endpoint detection and response (EDR) by unifying prevention, detection, response, and prediction across the network, cloud, and endpoints. It empowers the energy cooperatives with a holistic view of their security posture, thereby enabling quicker threat detection and response.
Enhanced Security
Leargas Security XDR provides an enhanced level of security through its multi-layered protection approach. It combines advanced AI algorithms, threat intelligence, and machine learning to detect, prevent, and respond to threats in real-time. This robust security framework protects energy cooperatives from a wide range of cyber threats, from ransomware to advanced persistent threats. The real-time detection and response capabilities minimize the impact of any potential cyber-attacks, thereby ensuring uninterrupted power supply to the communities they serve.
Streamlined Operations
Traditionally, energy cooperatives have relied on multiple security solutions, each operating in silos. Leargas Security XDR, with its unified approach, streamlines security operations by integrating all security functions into a single platform. This consolidation not only reduces the complexity of managing multiple tools but also improves operational efficiency by enabling a coordinated response to threats. Moreover, Leargas Security XDR's automation capabilities significantly reduce the workload of IT teams, allowing them to focus on strategic tasks.
Cost-Effective
For energy cooperatives, which often operate on tight budgets, Leargas Security XDR offers a cost-effective cybersecurity solution. By consolidating multiple security tools into one platform, it reduces the total cost of ownership. Furthermore, its predictive capabilities allow energy cooperatives to proactively address vulnerabilities before they are exploited, thereby avoiding the high costs associated with remediation and recovery from a cyber attack.
Regulatory Compliance
Energy cooperatives operate in a heavily regulated environment with strict cybersecurity requirements. Leargas Security XDR's comprehensive reporting and auditing tools make it easier for these cooperatives to demonstrate compliance with various regulatory standards. In addition, it offers features like data loss prevention and privacy protection, ensuring that cooperatives meet their data protection obligations.
Resilience and Reliability
Energy cooperatives form the backbone of many local communities, supplying essential power to residential homes, businesses, and public services. Any interruption in their service can have significant repercussions. By implementing Leargas Security XDR, cooperatives can ensure the resilience and reliability of their services. Its robust defense mechanisms and quick response capabilities mitigate the risk of power outages due to cyber-attacks, reinforcing the trust of community members in their cooperative.
In Closing
In the current era marked by escalating cyber threats, the worth of Leargas Security XDR within the context of energy cooperatives is immeasurable. This cutting-edge solution brings to the table enhanced security, a critical requirement for any organization but especially for those in the energy sector. The comprehensive, multi-layered security approach of Leargas Security XDR helps in identifying and neutralizing threats effectively and swiftly, thereby ensuring uninterrupted services.
Beyond robust security, Leargas Security XDR also presents other valuable benefits such as streamlined operations and cost-effectiveness. By integrating multiple security functionalities into a single platform, it simplifies the intricate process of managing diverse security solutions. This operational efficiency is not just about convenience; it directly translates into cost savings as well. In a sector where budget constraints are a constant reality, the financial advantage offered by Leargas Security XDR is undeniably significant.
Moreover, Leargas Security XDR helps energy cooperatives to remain compliant with the ever-stringent regulatory landscape. It also contributes towards improving the resilience of these organizations. By leveraging Leargas Security XDR, energy cooperatives can redirect their focus towards their primary mission—providing reliable and sustainable energy to their communities. The assurance that they are well-protected against the constantly evolving cyber threats brings a level of confidence that is indispensable in today's digitized world.
The Crucial Role of Zeek-based Platforms like Leargas Security XDR in IT and OT Environments

The fusion of Information Technology (IT) and Operational Technology (OT) ecosystems is increasingly becoming integral in today's enterprises. As the cyber threat landscape continues to evolve, posing intricate and sophisticated attacks, organizations are turning to advanced security solutions such as Leargas Security XDR. This potent platform, built on the robust Zeek framework, offers an all-in-one approach to securing IT and OT environments, providing vital insights and capabilities that help businesses stay ahead of potential threats. This article will delve into the significance of Zeek-based solutions like Leargas Security XDR with an emphasis on OT protocol analysis including DNP3, Modbus, and S7.
The Emergence of Zeek-based Solutions
Zeek, previously known as Bro, is an open-source network security monitoring platform highly acclaimed for its robust network traffic analysis capabilities. It provides a unique approach to network security, delivering comprehensive network activity information that aids in the effective detection, response, and prevention of cyber threats. Platforms such as Leargas Security XDR harness the power of Zeek, enhancing its capabilities with supplementary features and integrations to offer a sophisticated security solution.
Significance of Leargas Security XDR in Analyzing OT Protocols
1. Deep Visibility Into OT Protocols
Leargas Security XDR's ability to provide deep visibility into both IT and OT environments, particularly regarding OT protocols such as DNP3, Modbus, and S7, is one of its most powerful features. This profound visibility means that it's capable of monitoring and analyzing all the communication happening within a network, including both conventional IT data and specialized OT data.
OT protocols like DNP3, Modbus, and S7 are used extensively in industries such as energy, manufacturing, and transportation. They enable communication between devices and systems that control physical processes in these industries, such as Programmable Logic Controllers (PLCs), Remote Terminal Units (RTUs), and Industrial Control Systems (ICS). However, these protocols were designed for functionality and reliability, not security, which can make them potential targets for cyber threats.
Leargas Security XDR's monitoring capability is not merely passive; it actively inspects network traffic, generating a wealth of data on network activity, and then uses advanced analytics to turn that raw data into useful insights. This active monitoring includes OT protocols, which are often overlooked or inadequately covered by traditional IT-focused security tools.
By thoroughly inspecting network traffic related to DNP3, Modbus, and S7 protocols, Leargas Security XDR can identify anomalies, unusual patterns, or indicators of potential threats. For example, it might detect an unauthorized device attempting to communicate using one of these protocols, a sudden increase in network traffic that could indicate a Denial of Service (DoS) attack, or suspicious command sequences that could signal an attempt to disrupt physical processes.
This heightened visibility into OT protocols is invaluable for security teams. It not only gives them a more complete understanding of the organization's overall security posture but also enables them to more accurately identify potential threats in the OT environment. By recognizing threats early, organizations can respond more effectively, reducing the potential impact and preventing disruption to critical operations.
2. Advanced OT Protocol Threat Detection
Leargas Security XDR, built on the Zeek network security monitoring framework, goes beyond traditional threat detection methods by incorporating advanced techniques like machine learning and behavioral analytics. This approach allows the platform to detect patterns and anomalies within network traffic, with an emphasis on OT protocols such as DNP3, Modbus, and S7, which are commonly used in industries like energy, manufacturing, and transportation.
Machine learning is a subset of artificial intelligence that enables systems to learn from data, identify patterns, and make decisions with minimal human intervention. In the context of threat detection, machine learning algorithms are trained on vast amounts of network traffic data, learning to distinguish between normal and anomalous behaviors. Once trained, these algorithms can analyze new data, identify suspicious patterns, and flag potential threats.
Behavioral analytics, on the other hand, focuses on understanding the normal behavior of users, devices, and systems within the network. It monitors activities over time, establishing a baseline of what constitutes "normal" behavior. Once this baseline is established, the system can then detect any deviations from the norm, which could indicate a potential threat.
By combining machine learning and behavioral analytics, Leargas Security XDR can detect complex threats and subtle anomalies that might be overlooked by conventional security tools. For example, it could detect an unauthorized device attempting to communicate using an OT protocol, or a legitimate device suddenly behaving abnormally, perhaps due to being compromised. These subtle changes might be missed by a rule-based detection system, but with machine learning and behavioral analytics, Leargas Security XDR can identify these potential threats and alert the security team.
Furthermore, these advanced techniques enable the platform to adapt to evolving threats and changing network behaviors. As the machine learning algorithms continue to learn from new data, and the behavioral baselines are updated, the system becomes more effective at detecting threats over time.
This ability to detect threats that might otherwise be missed not only enhances the overall security of the organization but also allows for faster response times to incidents. By identifying potential threats early, organizations can take swift action to investigate and respond, thereby minimizing the impact of any security incident. In essence, Leargas Security XDR's use of progressive threat detection techniques significantly enhances the security posture of organizations, especially those with significant OT environments.
3. Unified Management
Security management in today's hybrid IT and OT environments can be complex and challenging. Each environment may use different systems, tools, and protocols, and the data generated can be voluminous and disparate. This is where Leargas Security XDR comes into play. It simplifies the task of security management by providing a unified platform that seamlessly integrates with various security tools and technologies, offering a centralized point of control and visibility.
When we say that Leargas Security XDR offers a 'unified platform,' we mean that it brings together data from diverse sources across the IT and OT environments, including network traffic data, logs from various systems and devices, threat intelligence feeds, and more. It consolidates this data into a single platform, making it easier to manage and analyze. This unified view is crucial for maintaining a holistic understanding of the organization's security landscape.
Moreover, Leargas Security XDR's integration capabilities play a critical role in simplifying security management. The platform is designed to integrate seamlessly with a wide range of security tools and technologies, such as intrusion detection systems, firewalls, endpoint protection solutions, and more. This integration allows for the correlation of data from different sources, enhancing the ability to detect complex threats that might be visible only when considering all the data together.
Centralized management, another key feature of Leargas Security XDR, streamlines various security tasks. With a single platform, security teams can efficiently manage security policies, ensuring consistency across the organization. Centralized management also simplifies incident response. When a potential threat is detected, the platform can alert the security team, who can then use the same platform to investigate the incident, determine the appropriate response, and track the response's implementation and effectiveness.
In addition, centralized management enables continuous monitoring of the organization's security posture. With all the security data in one place, security teams can easily generate reports, conduct audits, and identify areas where improvements are needed.
In summary, Leargas Security XDR simplifies security management across IT and OT environments by providing a unified, integrated platform for managing security data, policies, and incidents. This centralized approach enhances efficiency, improves threat detection and response, and supports a proactive, holistic approach to managing cybersecurity.
4. Streamlined Incident Response
Incident response is a crucial aspect of any organization's cybersecurity strategy. It involves the identification, investigation, and remediation of security incidents to minimize their potential impact. Leargas Security XDR empowers organizations to streamline this process through a combination of automation and actionable insights.
Automation plays a significant role in speeding up and improving the efficiency of the incident response process. With Leargas Security XDR, certain routine tasks can be automated, reducing the burden on security teams and allowing them to focus on more complex aspects of incident response. For instance, when a potential threat is detected, the platform can automatically gather relevant data, create an incident ticket, and notify the security team. In some cases, it can even implement predefined response actions, such as isolating a compromised system from the network to prevent the spread of a threat.
Actionable insights are another key feature of Leargas Security XDR that enhances incident response. By analyzing data from across the IT and OT environments, the platform can provide security teams with detailed insights into the nature of a security incident. This might include information about the systems or data affected, the nature of the threat, and potential remediation steps. These insights can help security teams make informed decisions and respond to incidents more effectively.
Moreover, Leargas Security XDR supports the entire incident response lifecycle, from identification through to remediation. By consolidating all incident-related information in one place, the platform enables security teams to quickly identify incidents, investigate them thoroughly, and implement appropriate remediation measures. This includes the ability to track the progress of incident response activities, assess their effectiveness, and make necessary adjustments.
In addition, the platform's advanced analytics capabilities can help identify patterns and trends in security incidents, providing valuable feedback that can be used to improve the organization's overall security posture. For example, if certain types of incidents are occurring frequently, this might indicate a need for additional training, changes to security policies, or improvements in security controls.
5. Scalability for OT Protocol Analysis
Scalability is a critical feature for any security platform, allowing it to adapt to the changing needs of an organization. As a business grows, so does the complexity and volume of its IT and OT environments, and with them, the potential security threats. Leargas Security XDR is designed to comfortably scale to meet these expanding needs, providing comprehensive security coverage for OT protocols in both large enterprises and smaller organizations.
Scalability in the context of Leargas Security XDR relates to several different aspects. First and foremost, it involves the ability to handle increasing volumes of data. As an organization grows, the amount of network traffic, the number of devices and systems, and the volume of logs and other security data all increase. Leargas Security XDR can scale to handle this increased data load, ensuring that all relevant data is collected, analyzed, and stored effectively.
Secondly, Leargas Security XDR's scalability relates to its ability to monitor an increasing number of OT protocols. Whether it's DNP3, Modbus, S7, or other industry-specific protocols, Leargas Security XDR is designed to provide comprehensive coverage for these protocols as they are introduced into the organization's OT environment.
Thirdly, the scalability of Leargas Security XDR is reflected in its capacity to integrate with a growing number of other security tools and technologies. As an organization's security infrastructure evolves, new tools may be added, requiring integration with the existing security platform. Leargas Security XDR's flexible architecture allows for these integrations, ensuring a seamless, unified security management experience.
Lastly, Leargas Security XDR's scalability also involves its ability to adapt to evolving security requirements. As cyber threats continue to become more sophisticated, security platforms need to be able to incorporate new detection and response capabilities. Leargas Security XDR is built on a flexible, extensible framework, allowing for the addition of new features and capabilities as needed.
Closing Out
The world of cybersecurity is becoming increasingly complex, marked by a growing interconnection between information technology (IT) and operational technology (OT) environments, and an evolving array of sophisticated threats. In this intricate landscape, the necessity for advanced security solutions like Leargas Security XDR cannot be overstated. With its distinct emphasis on OT protocol analysis, this platform offers capabilities that are paramount for securing modern organizations.
Harnessing the power of the Zeek network security monitoring framework, Leargas Security XDR provides a profound level of visibility into both IT and OT environments. Its ability to actively monitor and analyze network traffic, including OT protocols such as DNP3, Modbus, and S7, gives security teams an unprecedented level of insight. This deep visibility is essential for detecting anomalies, identifying potential threats, and ensuring a comprehensive understanding of the organization's security posture.
Further enhancing its threat detection capabilities, Leargas Security XDR employs advanced techniques like machine learning and behavioral analytics. This empowers the platform to identify patterns and anomalies in network traffic, including those within OT protocols that might be missed by traditional security tools. By detecting threats early, organizations can respond more effectively, reducing the potential impact of security incidents.
Leargas Security XDR also simplifies security management across the IT and OT environments by providing a unified platform. This platform seamlessly integrates with various security tools and technologies, offering centralized management of security data, policies, and incidents. The benefits of this unified approach include greater efficiency, improved threat detection and response, and a more proactive, holistic approach to managing cybersecurity.
Streamlining the incident response process is another key capability of Leargas Security XDR. Through automation of routine tasks and provision of actionable insights, the platform enables security teams to rapidly identify, investigate, and remediate security incidents. By reducing the time to resolution, this streamlined process minimizes potential damage and ensures a swift return to normal operations.
Lastly, Leargas Security XDR offers scalability to meet the expanding needs of businesses, regardless of their size. As organizations grow and their security requirements evolve, Leargas Security XDR can adapt, providing comprehensive security coverage for an expanding range of OT protocols and integrating with a growing number of other security tools.
As we move further into an era marked by increasing digitalization and interconnectivity, the threat landscape becomes more complex. Investment in advanced, Zeek-based security platforms like Leargas Security XDR is key to ensuring the security and resilience of organizations' IT and OT infrastructures. It's a strategic move that positions organizations to confront the evolving cyber threats head-on, safeguarding their critical operations and assets.
SCHEDULE A DEMO
Experience the power of Léargas XDR
Unlock the future of cybersecurity with a hands-on experience of Léargas XDR. Our cutting-edge platform is designed to proactively detect, investigate, and block security threats in real-time.
Now, it's your turn to witness its capabilities in action.

© Copyright Léargas Security. All Rights Reserved.
